What Is SOC 2 Compliance? Types, Criteria, and Checklist


What Is SOC 2 Compliance? Types, Criteria, and Checklist
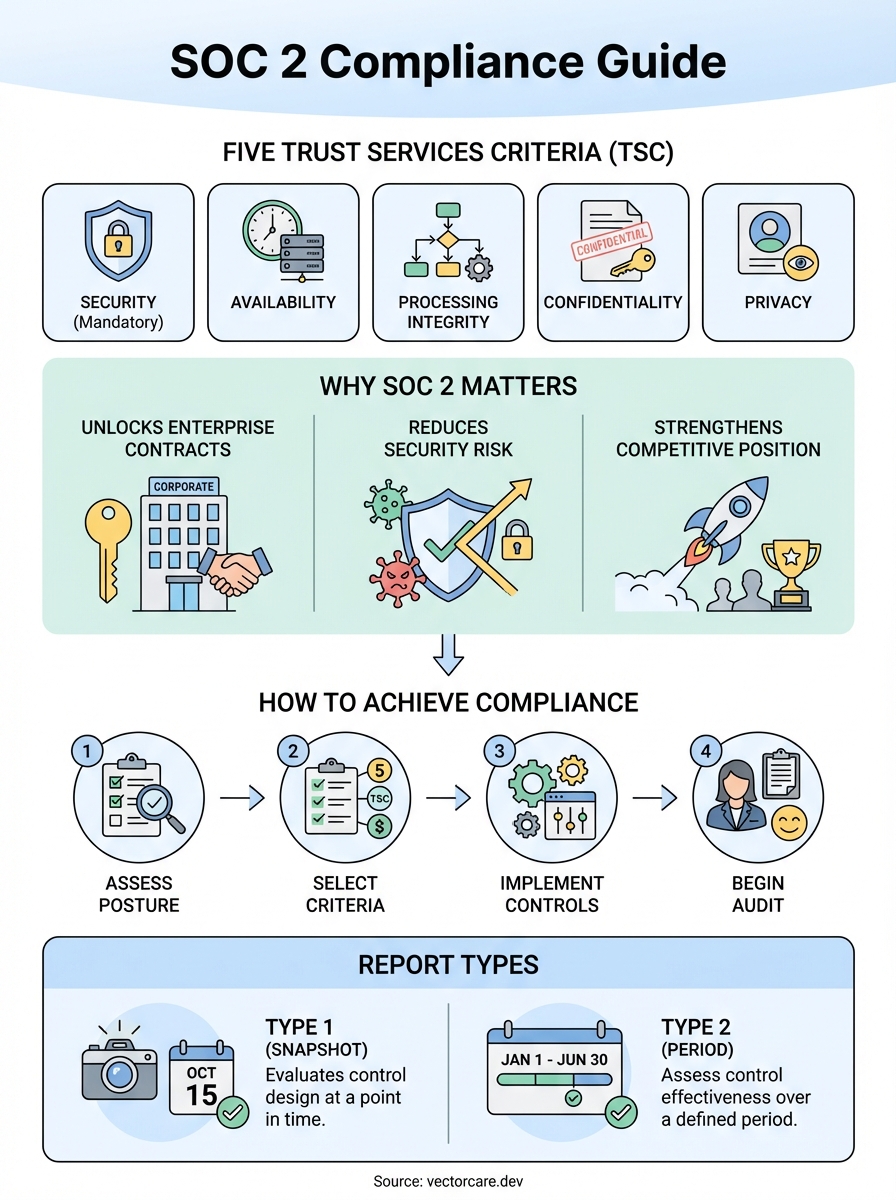
SOC 2 compliance is a security framework that proves your organization handles customer data responsibly. When you work with healthcare vendors or enterprise clients, they want to know their sensitive information is safe in your hands. SOC 2 gives them that assurance through an independent audit of your security controls, policies, and procedures. The framework focuses on five core areas called Trust Services Criteria. These include security, availability, processing integrity, confidentiality, and privacy. Think of it as a detailed report card that shows potential customers exactly how you protect their data.
This guide breaks down everything you need to know about SOC 2 compliance. You'll learn why it matters for healthcare vendors and SaaS companies, understand the difference between Type 1 and Type 2 reports, and explore each Trust Services Criteria in detail. We'll also walk through the practical steps to achieve compliance and share a checklist you can follow. Whether you're preparing for your first audit or trying to understand what your customers are asking for, this article gives you the clarity you need to move forward with confidence.
Why SOC 2 compliance matters
Your potential customers want proof that you protect their data before they sign a contract. Healthcare vendors face this reality every day when pursuing partnerships with health systems and enterprise organizations. These buyers won't risk their reputation or patient data on a vendor that can't demonstrate solid security practices. SOC 2 compliance answers their concerns with an independent audit that validates your security controls. Without it, you'll struggle to get past the procurement process at mid-sized and large organizations.

It unlocks enterprise contracts
Enterprise customers and health systems typically require SOC 2 reports during their vendor evaluation process. Their security teams review these reports to assess whether your systems meet their internal standards. You'll face immediate disqualification if you can't provide this documentation when requested. Healthcare organizations take this requirement especially seriously because they handle protected health information (PHI) that falls under HIPAA regulations. A SOC 2 report demonstrates that you've implemented the technical and organizational controls necessary to safeguard sensitive data. This speeds up contract negotiations and removes a major barrier to closing deals.
SOC 2 compliance transforms from a nice-to-have into a must-have the moment you start selling to enterprise customers.
It reduces security risk
The process of achieving SOC 2 compliance forces you to identify gaps in your security posture before a breach exposes them. You'll implement formal policies for access control, data encryption, incident response, and system monitoring. These controls protect your business from costly data breaches that can destroy customer trust and result in regulatory fines. When you understand what is SOC 2 compliance and apply it to your operations, you create a foundation of security practices that mature with your company. Your team gains clarity on security responsibilities, and your systems become more resilient against threats.
It strengthens your competitive position
Vendors with SOC 2 reports win more deals than competitors who lack this certification. You can market your compliance status on your website, in sales materials, and during customer conversations. This differentiation becomes particularly valuable in crowded markets where buyers struggle to distinguish between similar solutions. Your sales cycle shortens because procurement teams spend less time evaluating your security measures. You'll also face fewer security questionnaires and ad-hoc audits from individual customers, saving your team significant time and resources.
How to achieve SOC 2 compliance
Achieving SOC 2 compliance requires you to implement specific security controls, document your policies, and undergo an independent audit. The process typically takes three to six months for organizations with basic security practices already in place. You'll need to demonstrate that your systems protect customer data according to the Trust Services Criteria established by the American Institute of Certified Public Accountants (AICPA). The timeline extends longer if you lack foundational controls like access management, encryption, or incident response procedures. Your preparation determines how smoothly the audit process runs and how quickly you can share your SOC 2 report with prospects.
Assess your current security posture
You need to understand where your security controls stand before you can close any gaps. Start by conducting a readiness assessment that evaluates your existing policies, technical controls, and operational procedures against SOC 2 requirements. This assessment reveals which controls you already have in place and which ones require implementation or improvement. Many organizations discover they have informal security practices that need formal documentation and consistent enforcement. You can perform this assessment internally or hire a consultant to guide you through the process. The assessment creates a roadmap that prioritizes the most critical gaps and estimates the effort required to address them.
Select your Trust Services Criteria
Your first major decision involves choosing which Trust Services Criteria to include in your SOC 2 audit scope. Security is mandatory for all SOC 2 reports, but you can add availability, processing integrity, confidentiality, and privacy based on your business model and customer needs. Healthcare vendors typically include security and confidentiality at minimum because they handle sensitive patient information. Your customers may specifically request certain criteria in their vendor requirements, so review your contracts and RFP responses before making this decision. Adding more criteria increases the audit scope and cost, but it also provides broader assurance to your customers.
The criteria you select should align with the promises you make to customers about how you protect and process their data.
Implement required controls
Implementation involves establishing the technical and organizational controls that satisfy SOC 2 requirements. You'll create formal security policies, configure access controls, enable encryption for data at rest and in transit, implement logging and monitoring systems, and establish incident response procedures. Your team needs to document each control and collect evidence that demonstrates the control operates effectively. This evidence includes screenshots, configuration files, logs, and policy acknowledgments from employees. You should implement controls at least 90 days before your audit begins to establish an operating history that auditors can evaluate. Many organizations use compliance management platforms to automate evidence collection and track control implementation progress.
Choose an auditor and begin the audit
You must work with a licensed CPA firm that specializes in SOC 2 audits to obtain your report. Research potential auditors by asking for referrals from other healthcare vendors, reviewing their experience with companies similar to yours, and comparing their pricing and timeline estimates. Once you select an auditor, they'll conduct a scoping call to understand your systems, review your control implementation, and plan the audit fieldwork. The audit itself involves the auditor testing your controls, reviewing evidence, interviewing your team members, and documenting their findings. After completing fieldwork, the auditor issues your SOC 2 report, which you can then share with customers and prospects to demonstrate your commitment to data security.
SOC 2 trust services criteria explained
The Trust Services Criteria form the foundation of what is SOC 2 compliance and determine exactly what your auditor will evaluate during the audit process. These five criteria provide a framework for assessing how well your organization protects customer data and maintains system reliability. Your audit scope must include security as the baseline requirement, while you can add the other four criteria based on your business operations and customer commitments. Each criterion addresses specific aspects of data protection and system performance that matter to your customers and stakeholders.

Security (mandatory for all reports)
Security forms the mandatory core of every SOC 2 report because it addresses the fundamental protection of your systems against unauthorized access. Your auditor evaluates whether you've implemented access controls, network security, encryption, and monitoring systems to prevent data breaches. This criterion examines your authentication methods, password policies, firewall configurations, intrusion detection systems, and how you grant and revoke employee access to sensitive systems. Healthcare vendors need particularly strong security controls because they handle protected health information that requires stringent safeguards under HIPAA regulations.
Security controls protect the entire foundation of your customer relationships by preventing unauthorized access to the systems and data you manage.
Availability
Availability measures whether your systems and services remain accessible when customers need them. Your auditor reviews your infrastructure redundancy, disaster recovery plans, backup procedures, and monitoring systems that detect outages. This criterion matters most for SaaS platforms and critical healthcare applications where downtime directly impacts clinical workflows or patient care. You'll need to document your uptime commitments, incident response procedures, and how you handle system failures to maintain service continuity.
Processing integrity
Processing integrity ensures that your systems process data completely, accurately, and in a timely manner. Your auditor examines quality controls that prevent errors, validate data inputs, detect processing failures, and verify that transactions complete as intended. Healthcare vendors who calculate dosages, process claims, or analyze patient data should include this criterion because accuracy directly impacts patient safety and clinical decision-making. You demonstrate processing integrity through automated validation checks, error handling procedures, and monitoring systems that detect anomalies in your data processing workflows.
Confidentiality
Confidentiality addresses how you protect information designated as confidential beyond the general security controls that apply to all data. Your auditor evaluates the additional safeguards you implement for trade secrets, intellectual property, and sensitive business information that customers share with you. This criterion requires you to classify data based on sensitivity levels, implement access restrictions that limit who can view confidential information, and document how you handle confidential data throughout its lifecycle. Most healthcare vendors include confidentiality in their scope because they process proprietary clinical protocols and business-sensitive patient information.
Privacy
Privacy examines whether you collect, use, retain, disclose, and dispose of personal information according to your privacy notice and applicable regulations. Your auditor reviews your consent mechanisms, data subject rights procedures, cross-border data transfer controls, and how you respond to privacy requests. You need this criterion if you handle personal information that falls under regulations like GDPR, CCPA, or HIPAA. Healthcare organizations typically require vendors to include privacy in their SOC 2 scope because patient data requires explicit privacy protections beyond basic security measures.
SOC 2 type 1 and type 2 reports
Your choice between a Type 1 and Type 2 report determines how deeply your auditor examines your security controls and what level of assurance you provide to customers. Both report types evaluate the same Trust Services Criteria, but they differ significantly in scope, timeline, and the evidence they provide about your control effectiveness. Understanding what is SOC 2 compliance means knowing which report type matches your business needs and customer expectations. Healthcare vendors typically face pressure from health system procurement teams to provide Type 2 reports because they demonstrate sustained commitment to security rather than a snapshot in time.
What Type 1 reports evaluate
Type 1 reports examine whether your security controls exist and function properly at a single point in time. Your auditor reviews your policies, tests your controls, and documents their findings based on a specific date you choose for the audit. This approach verifies that you designed your controls appropriately and implemented them correctly, but it doesn't assess whether you consistently operate those controls over weeks or months. Type 1 reports take less time to complete and cost less than Type 2 audits, making them attractive for organizations that need compliance quickly. However, many enterprise customers and health systems reject Type 1 reports because they want evidence of ongoing control operation rather than a momentary assessment.
What Type 2 reports evaluate
Type 2 reports assess how effectively your controls operate over a defined period, typically between three and twelve months. Your auditor examines whether you consistently followed your security policies, maintained your technical controls, and addressed any issues that arose during the audit period. They test control operation multiple times throughout the period to verify sustained effectiveness rather than accepting a single test result. This comprehensive evaluation requires you to collect continuous evidence through logs, screenshots, policy acknowledgments, and incident reports that span the entire audit window. Most organizations select a six-month audit period to balance the thoroughness of evaluation with the time investment required.
Type 2 reports carry significantly more weight with enterprise buyers because they prove you maintain security controls consistently rather than activating them only for audit day.
Choosing between Type 1 and Type 2
You should pursue a Type 2 report if your target customers include enterprise organizations or health systems that make vendor security a priority in their procurement process. These buyers typically require Type 2 reports in their vendor questionnaires and contract terms, and providing a Type 1 report often delays or blocks deal progression. Your sales team can confirm whether prospects ask specifically for Type 2 reports during security reviews. Consider starting with Type 1 only if you need compliance immediately to close an urgent deal, but plan to upgrade to Type 2 for your next audit cycle. The cost difference between report types becomes negligible when you factor in the deal velocity and win rate improvements that Type 2 reports deliver for enterprise sales motions.

SOC 2 checklist for SaaS and health tech
Your preparation for SOC 2 compliance requires systematic implementation of security controls across multiple areas of your organization. Healthcare vendors and SaaS companies share similar compliance needs because both handle sensitive customer data that requires protection. This checklist breaks down what is SOC 2 compliance into specific tasks you can assign to your team and track through completion. You'll move faster through the audit process when you address these items methodically rather than scrambling to implement everything at once. The items listed here apply to both Type 1 and Type 2 audits, though Type 2 requires you to collect evidence continuously over your audit period.

Document your security policies
You need formal written policies that define how your organization handles security, even if you've been following these practices informally for months. Your information security policy serves as the foundation document that outlines your overall approach to protecting systems and data. Create specific policies for access control, password requirements, data encryption, incident response, vendor management, and employee onboarding and offboarding. Each policy should specify who owns it, when you review it, and how employees acknowledge they've read and understood it. Healthcare vendors must ensure these policies address HIPAA requirements in addition to SOC 2 criteria. Store all policies in a central location where employees can access them and auditors can review them during fieldwork.
Configure technical controls
Your systems need specific security configurations that your auditor will test during the assessment. Enable multi-factor authentication (MFA) on all administrative accounts and ideally on all employee accounts that access production systems. Implement encryption for data in transit using TLS 1.2 or higher and encrypt data at rest using AES-256 or equivalent standards. Configure your firewalls to restrict inbound traffic to only necessary ports and protocols, and segment your network to isolate production systems from internal networks. Set up centralized logging that captures authentication attempts, system changes, and access to sensitive data, and retain these logs for at least 90 days. Deploy endpoint protection on all employee devices and maintain an inventory of all hardware and software assets your team uses to access or process customer data.
Technical controls form the backbone of your security program by preventing unauthorized access before it becomes a data breach.
Establish operational procedures
Operational procedures define how your team executes security tasks consistently across your organization. Create a process for provisioning and deprovisioning user accounts that documents approval workflows, timing requirements, and access review schedules. Implement change management procedures that require testing, approval, and documentation before deploying code or configuration changes to production. Develop an incident response plan that specifies detection methods, escalation paths, communication protocols, and post-incident review requirements. Schedule quarterly access reviews where managers verify that employees still need their current system permissions. Healthcare vendors should include procedures for handling Business Associate Agreements and responding to patient data requests under HIPAA.
Prepare for the audit
Audit preparation involves collecting evidence that proves your controls operate effectively. Create a shared folder structure where you store screenshots, configuration exports, policy acknowledgments, and meeting notes organized by control area. Schedule monthly evidence collection sessions where designated team members gather required documentation rather than waiting until the audit begins. Conduct internal testing of your controls to identify gaps before your auditor finds them, and document any exceptions or control failures along with your remediation steps. Select your auditor at least 60 days before you want to complete fieldwork to allow time for scoping discussions and planning. Your audit readiness improves dramatically when you treat evidence collection as an ongoing practice rather than a last-minute scramble.
Common SOC 2 questions and misconceptions
Healthcare vendors and SaaS companies often misunderstand what is SOC 2 compliance and what it actually requires. You'll encounter misleading information from competitors, consultants, and even potential customers who use imprecise terminology when discussing compliance. These misconceptions can lead you to make poor decisions about your compliance strategy, budget more time or money than necessary, or explain your compliance status incorrectly to prospects. Clearing up these common questions helps you set realistic expectations and communicate your security posture accurately to customers and stakeholders.
Is SOC 2 a certification?
SOC 2 represents an attestation, not a certification, despite how commonly people use the wrong term. You receive an audit report that documents your auditor's findings about your security controls rather than earning a certificate from a governing body. The American Institute of Certified Public Accountants establishes the SOC 2 framework, but they don't certify individual organizations. Your auditor issues an opinion on whether your controls satisfy the Trust Services Criteria based on evidence collected during fieldwork. This distinction matters when you communicate with customers because claiming certification suggests a level of formal approval that doesn't exist in the SOC 2 process.
Can you fail a SOC 2 audit?
Your auditor doesn't issue pass or fail determinations in the traditional sense. Instead, they provide one of four opinion types: unqualified (clean), qualified (with exceptions), adverse (significant deficiencies), or disclaimer (insufficient information). Most organizations receive qualified opinions that note specific control gaps or failures while affirming that most controls operate effectively. You can still share a qualified report with customers, though they'll review the exceptions carefully to assess whether those gaps create unacceptable risks. Organizations rarely receive adverse opinions because auditors usually identify major deficiencies early and recommend delaying the audit until you remediate them.
Your audit report documents your actual security posture rather than declaring whether you passed an arbitrary threshold.
Does SOC 2 guarantee perfect security?
SOC 2 compliance demonstrates that you've implemented reasonable security controls based on industry standards, but it doesn't prevent all possible security incidents. Your auditor evaluates whether controls exist and operate effectively at the time of the audit, not whether those controls will stop every future attack. You'll still face security threats from sophisticated attackers, zero-day vulnerabilities, and human error despite maintaining SOC 2 compliance. The framework reduces your risk significantly by establishing baseline security practices, but you need additional security measures and ongoing vigilance to protect customer data comprehensively.
Next steps with SOC 2 compliance
You now understand what is SOC 2 compliance and how it impacts your ability to sell to healthcare organizations and enterprise customers. The framework requires significant time and resources to implement properly, but it unlocks enterprise contracts that drive sustainable revenue growth for your business. Your team needs to prioritize security controls, document comprehensive policies, collect evidence continuously throughout your audit period, and work with a qualified CPA firm to obtain your final report. Healthcare vendors face additional complexity because they must align SOC 2 requirements with HIPAA regulations and EPIC integration standards that health systems demand from their technology partners.
VectorCare handles SOC 2 compliance as part of our managed SMART on FHIR platform, removing this burden from your engineering team entirely. You can focus on building your core product while we manage the technical infrastructure, security controls, and compliance requirements that procurement teams require from modern healthcare vendors.
The Future of Patient Logistics
Exploring the future of all things related to patient logistics, technology and how AI is going to re-shape the way we deliver care.