SOC 2 Type I vs Type II: Differences, Timeline, and Costs


SOC 2 Type I vs Type II: Differences, Timeline, and Costs
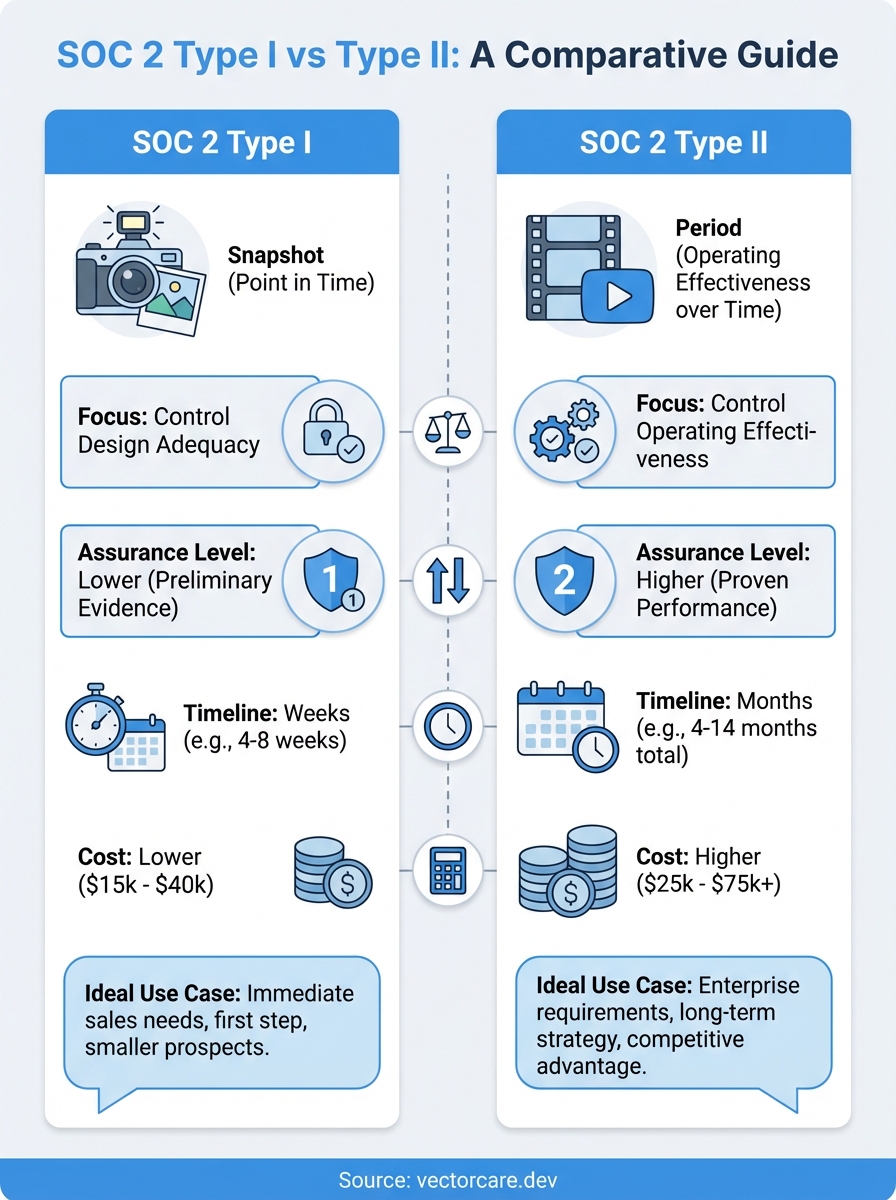
SOC 2 Type I and Type II are two different audit reports that prove your company handles customer data securely. Type I checks if your security controls are designed properly at a single point in time. Think of it as a snapshot that shows you built the right safeguards. Type II goes further by testing whether those controls actually work as intended over a period of several months. It demonstrates that your security measures hold up under real operating conditions. Both reports assess the same Trust Services Criteria but differ significantly in scope, duration, and the level of assurance they provide to customers and partners.
This guide breaks down the practical differences between these two audit reports. You'll learn how each audit works, what evidence auditors examine, how long the process takes, and what you'll pay at each stage. We'll cover the key decision factors that matter most when choosing between Type I and Type II compliance, including your business timeline, customer requirements, and budget constraints.
Why SOC 2 Type I and Type II matter
Healthcare vendors pursuing SOC 2 Type I or Type II face a simple reality: enterprise customers and health systems won't sign contracts without proof of data security. Your potential clients need concrete evidence that you protect patient information and meet industry standards for handling sensitive data. A SOC 2 report serves as that proof, demonstrating that independent auditors verified your security controls according to established criteria. Without this documentation, you'll lose deals to competitors who completed the audit process, regardless of how strong your actual security practices might be.
Customer requirements drive adoption
Large healthcare organizations maintain strict vendor requirements that include SOC 2 attestation as a non-negotiable prerequisite. Your sales team will encounter security questionnaires and procurement checklists that specifically ask for SOC 2 reports during the contracting phase. Health systems face regulatory pressure to verify that every vendor in their ecosystem maintains adequate security controls, which means they transfer that burden to you through formal requirements. Missing this credential stops your sales process before technical evaluations or pricing discussions even begin.

Enterprise healthcare buyers expect vendors to demonstrate security compliance through recognized audit frameworks, not just internal assurances.
Market advantage and trust signals
Organizations with SOC 2 compliance close deals faster and win larger contracts than those without it. Your buyers view the audit report as independent validation of your security posture, which reduces their perceived risk when selecting your solution. The certification also positions your company as a mature, trustworthy vendor capable of meeting healthcare industry standards. Investors and partners consider SOC 2 status when evaluating your business, making it a valuable asset beyond customer acquisition. You gain competitive differentiation in crowded markets where multiple vendors offer similar features but vary in their commitment to security standards.
How to decide between SOC 2 Type I and Type II
Choosing between SOC 2 Type I and Type II requires you to evaluate your immediate business needs against long-term compliance goals. Your decision impacts how quickly you can close deals, how much budget you'll allocate to compliance, and what level of assurance you provide to customers. Most healthcare vendors face specific circumstances that make one option more practical than the other, based on factors like sales pipeline timing, customer requirements, and operational readiness.
Assess your timeline urgency
Type I audits deliver results in weeks rather than months, making them ideal when you need compliance certification to unlock immediate sales opportunities. You should pursue Type I if a major health system prospect requires SOC 2 documentation to finalize a contract within the next quarter. The faster turnaround lets you demonstrate security controls without waiting six to twelve months for Type II completion. However, recognize that Type I serves as a stepping stone rather than a permanent solution, since many enterprise customers eventually request the more comprehensive Type II report.

Type II audits require patience but eliminate the need for a second audit cycle down the road. Your organization benefits from Type II when you have established controls running consistently for at least three months and can afford a longer audit timeline. Starting with Type II saves money compared to conducting separate Type I and Type II audits sequentially. Healthcare vendors with stable operations and no immediate sales deadlines often skip Type I entirely to avoid duplicate audit fees.
Evaluate customer expectations
Your target customers dictate which report type you ultimately need. Enterprise health systems typically require Type II reports because they want proof that your security controls function effectively over time, not just exist on paper. Smaller healthcare organizations or early-stage health systems may accept Type I initially but will request Type II as your business relationship matures. Survey your current prospects and existing customers to identify their specific compliance requirements before committing to an audit path.
Organizations that start with Type I often face customer pressure to upgrade to Type II within twelve months, resulting in higher total costs.
Consider your budget constraints
Type I audits cost less upfront because auditors spend fewer hours examining your controls. You'll pay for control design assessment without the extensive testing required for Type II. Type II audits carry higher initial costs due to the extended audit period and deeper testing requirements, but they provide stronger market positioning. Calculate whether paying for both audits separately exceeds the cost of going straight to Type II. Healthcare vendors operating on tight budgets sometimes choose Type I to start generating revenue faster, then fund Type II with incoming customer contracts.
Key differences between SOC 2 Type I and Type II
The fundamental distinction between SOC 2 Type I and Type II centers on what auditors examine and how they verify your security controls. Type I auditors review your control documentation and interview your team to confirm that security measures exist and follow logical design principles. They check whether you documented policies, configured systems correctly, and established procedures that should theoretically protect customer data. Type II auditors perform all those Type I activities but add extensive testing to verify that your controls actually work in practice over several months. Your organization faces different preparation requirements, audit experiences, and customer perceptions based on which report type you pursue.

Audit scope and control assessment
Type I audits focus exclusively on control design at a specific date, typically the final day of your readiness period. Auditors evaluate whether your documented controls align with Trust Services Criteria requirements for security, availability, processing integrity, confidentiality, or privacy. They verify that you identified risks, mapped controls to those risks, and implemented systems that should address security threats. Your team demonstrates controls through screenshots, policy documents, and system configurations captured at that single point in time.
Type II audits expand beyond design assessment to examine how controls performed throughout an observation period. Auditors select a representative sample of control instances to test, reviewing logs, tickets, access reports, and change records from across the audit window. Your organization must prove that controls operated consistently according to documented procedures, not just that you designed them correctly. This testing reveals whether your team actually followed security policies, whether automated controls triggered as configured, and whether manual processes occurred on schedule.
Operating effectiveness requirements
Type I reports contain no operating effectiveness testing because auditors only verify that controls exist and appear properly structured. Your organization receives attestation that controls were suitably designed as of the audit date, which tells customers you built appropriate safeguards but not whether they function reliably. Health system buyers understand this limitation and often view Type I as preliminary evidence of security maturity.
Type II reports provide measurably stronger assurance because they demonstrate sustained control performance rather than theoretical design quality.
Type II auditors test whether controls achieved their intended outcomes throughout the entire audit period. They examine failure rates, exception handling, and remediation timelines to assess operational reliability. Your team must show that backup procedures completed successfully, access reviews occurred quarterly as documented, and vulnerability scans ran on schedule without gaps. Auditors identify control deviations or exceptions in the report, documenting any instances where controls failed to operate as designed.
Evidence collection and documentation depth
Type I evidence requirements include current policy documents, system configuration screenshots, and organizational charts showing security roles. You provide point-in-time proof that controls existed on the audit date through network diagrams, access control matrices, and recent security assessments. Auditors request samples of key documents but don't need continuous logs or historical records spanning multiple months.
Type II evidence demands comprehensive historical documentation covering the full audit window, typically six to twelve months. Your organization must retain and produce access logs, change management tickets, training completion records, incident response reports, and monitoring alerts from across the entire period. Auditors sample multiple instances of recurring controls to verify consistent execution. You'll gather substantially more evidence for Type II audits, including quarterly access reviews, monthly vulnerability reports, and continuous system monitoring logs that prove ongoing control effectiveness.
Report content and customer value
Type I reports describe your control environment and provide the auditor's opinion on design adequacy. Customers receive a shorter document that explains your security framework but contains no testing results or effectiveness validation. Type II reports include everything from Type I plus detailed testing procedures, sample sizes, and results for each control tested. Your prospects gain deeper insight into security performance through exception reporting and auditor observations about control maturity. Healthcare organizations conducting vendor risk assessments find Type II reports significantly more valuable because they demonstrate proven security operations rather than untested control design.
Timeline for SOC 2 Type I vs Type II audits
Understanding the timeline differences between SOC 2 Type I vs Type II helps you plan your compliance journey and set realistic expectations with customers. Your audit duration directly impacts when you can start closing deals, how long your team dedicates resources to compliance, and when you'll need to budget for audit expenses. Healthcare vendors often underestimate the total time from initial preparation through final report delivery, which creates problems when sales teams promise compliance dates to prospects.

Type I audit duration
Type I audits typically require four to eight weeks from kickoff to final report delivery, assuming your controls are already documented and operational. You spend the first two weeks gathering evidence, conducting auditor interviews, and preparing documentation that proves your controls exist. Auditors then perform their fieldwork over one to two weeks, reviewing your evidence and testing control design. Your organization receives a draft report for management review, which takes another week to finalize. Fast-track options exist when urgent sales opportunities demand quicker certification, but rushing the process increases the risk of findings or exceptions that require remediation before report issuance.
Type II audit timeline components
Type II audits span a minimum observation period of three to six months, with many healthcare vendors choosing six to twelve months for stronger market positioning. Your audit clock starts on the first day of the observation period, during which you operate controls consistently while collecting evidence. Auditors don't begin intensive fieldwork until the observation period ends, at which point they spend three to six weeks testing sampled control instances from across the entire window. The total timeline from observation start to final report ranges from four to fourteen months depending on your chosen observation period length and auditor scheduling.
Type II timelines extend significantly beyond Type I because auditors must validate sustained control performance rather than point-in-time design quality.
Planning your audit schedule
You should begin preparation three to six months before launching either audit type to ensure controls operate properly and evidence collection systems function correctly. Healthcare vendors pursuing Type I often transition immediately into Type II by starting their observation period on the same day they receive Type I certification. Your team needs to coordinate audit timing with major product releases, organizational changes, or system migrations that might disrupt control operations. Schedule your audit to complete before critical sales milestones or contract renewal deadlines that require SOC 2 documentation.
Costs of SOC 2 Type I vs Type II compliance
Cost differences between SOC 2 Type I vs Type II stem from audit complexity, observation period length, and evidence testing requirements. Your organization pays auditors for the hours they spend reviewing documentation, testing controls, and writing reports, which means Type II audits always cost more due to extended engagement duration. Healthcare vendors should budget for both direct audit fees and internal resource costs, including staff time dedicated to evidence collection, policy development, and auditor support. Understanding the complete cost structure helps you allocate budget appropriately and avoid surprises during the compliance process.
Type I cost breakdown
Type I audits typically range from $15,000 to $40,000 depending on your organization size, system complexity, and number of Trust Services Criteria in scope. Your base audit fee covers auditor hours for design assessment, evidence review, and report preparation. You'll also invest in preparation costs including documentation tools, policy templates, and potential consultant fees if your team lacks compliance experience. Internal staff time represents a hidden cost, with your security and operations teams dedicating 100 to 200 hours gathering evidence, conducting interviews, and responding to auditor requests.
Type II cost investment
Type II audits command higher fees ranging from $25,000 to $75,000 or more, reflecting the extended observation period and comprehensive testing requirements. Your auditor bills additional hours for sampling control instances, reviewing logs from across multiple months, and documenting testing procedures. Ongoing evidence collection throughout the observation period requires dedicated tools or staff resources to maintain compliance tracking systems. Healthcare vendors often underestimate the cumulative internal cost of sustaining controls and gathering evidence over six to twelve months, which can equal or exceed the auditor's direct fees.
Organizations that pursue Type I followed by Type II within twelve months typically spend 40 to 60 percent more than those who start directly with Type II.
Budget planning factors
Your total compliance investment extends beyond auditor fees to include technology infrastructure, security tools, and personnel training needed to meet SOC 2 requirements. You'll likely purchase or upgrade monitoring systems, access management platforms, and backup solutions to satisfy control requirements. Factor in remediation costs for any gaps auditors identify during readiness assessments, which might require new software licenses or additional security staff. Healthcare vendors should budget $10,000 to $30,000 annually for ongoing compliance maintenance, including continuous monitoring tools, policy updates, and annual audit renewal fees.
Next steps for SOC 2 Type I and II
Your decision between SOC 2 Type I vs Type II should align with your immediate sales pipeline and long-term compliance strategy. Start by assessing your current control environment and documenting existing security measures before engaging auditors. Healthcare vendors typically need three to six months of preparation time to establish controls, train staff, and implement evidence collection systems that support either audit type.
Organizations pursuing EPIC EHR integration face additional compliance pressure since health systems expect vendors to maintain SOC 2 certification alongside SMART on FHIR standards. You'll need to coordinate your audit timeline with product development cycles and customer implementation schedules to avoid delays. Build and deploy your SMART on FHIR app with compliance built into the platform, reducing the engineering burden while maintaining the security controls healthcare customers require.
The Future of Patient Logistics
Exploring the future of all things related to patient logistics, technology and how AI is going to re-shape the way we deliver care.