AICPA SOC 2 Guide: Criteria, Controls, and Reporting Playbook


AICPA SOC 2 Guide: Criteria, Controls, and Reporting Playbook
You need SOC 2 compliance to win healthcare contracts. But when you open the AICPA SOC 2 Guide, you face 300 pages of attestation standards, trust services criteria, and examination procedures. Most vendors get stuck trying to translate abstract requirements into actual controls their auditor will accept.
The AICPA publishes the official SOC 2 Guide to help CPAs perform examinations of service organizations. But you can use this same framework to build your compliance program from scratch. The 2022 edition incorporates SSAE 21 standards and revised trust services criteria that define what auditors evaluate during your examination.
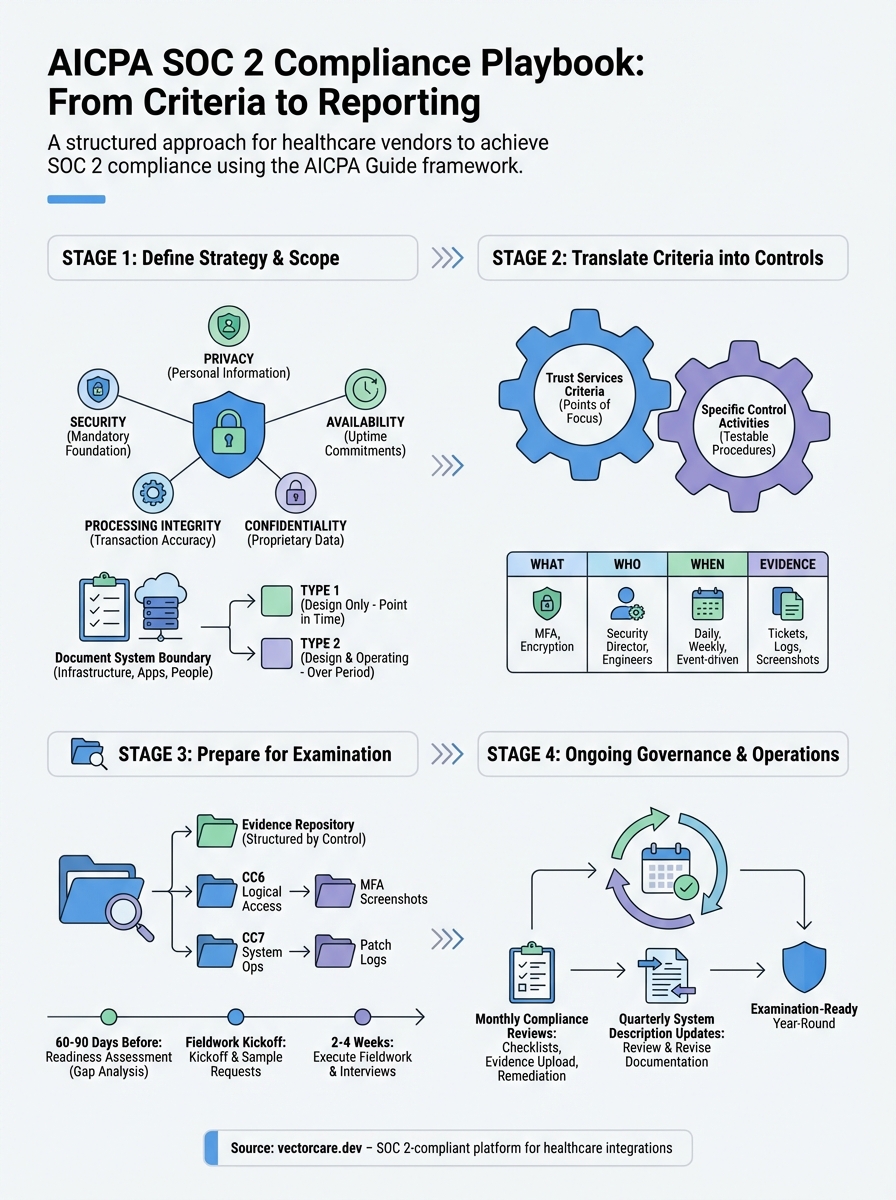
This playbook breaks down the AICPA SOC 2 Guide into five practical stages. You'll learn how to define your examination scope, map the five trust services criteria to specific controls, prepare evidence for your auditor, and maintain compliance after your report. Each section includes implementation guidance from the 2022 criteria revisions so you can build a program that passes examination the first time.
What the AICPA SOC 2 guide is
The AICPA SOC 2 Guide is the authoritative examination manual that CPAs use when evaluating your organization's security, availability, processing integrity, confidentiality, and privacy controls. Published as "Reporting on an Examination of Controls at a Service Organization Relevant to Security, Availability, Processing Integrity, Confidentiality, or Privacy," this document defines the attestation standards your auditor follows during your examination. You can purchase the guide directly from the AICPA website as either a digital download or print-on-demand version.

The official examination framework
The guide serves as the implementation roadmap for SSAE 21 attestation standards and the 2017 Trust Services Criteria (revised 2022). Your auditor references this document to determine which evidence samples they need, how to evaluate your control design, and what qualifies as an effective operating control. The guide includes illustrative reports that show exactly what your final SOC 2 report will contain, plus management representation letters and system description requirements.
"The guide provides the authoritative procedures and guidance for performing and reporting on SOC 2 examinations."
What's inside the 2022 edition
You'll find 12 chapters covering the complete examination lifecycle. Chapter 3 explains the five trust services categories (security, availability, processing integrity, confidentiality, privacy) you can include in your scope. Chapter 6 details the risk assessment process your auditor uses to determine which controls to test. Chapters 8 through 10 walk through evidence gathering, control testing, and report writing. The appendices contain the 2018 Description Criteria that define how you document your system, plus illustrative reports for both Type 1 (design only) and Type 2 (design and operating effectiveness) examinations.
Step 1. Define your SOC 2 strategy and scope
You start by defining which trust services categories your examination will cover and what systems fall within your system boundary. The AICPA SOC 2 Guide requires every examination to include the security category, but you choose whether to add availability, processing integrity, confidentiality, or privacy based on what your customers need. This decision shapes your entire compliance program because each category adds specific control requirements your auditor will test.

Choose your trust services categories
The security category is always mandatory because it forms the foundation for all other categories. You evaluate whether to include the four optional categories by reviewing your customer contracts and the services you provide. Healthcare vendors typically need security plus confidentiality and privacy to meet HIPAA requirements, while SaaS platforms often add availability to demonstrate uptime commitments.
| Trust Services Category | When to Include |
|---|---|
| Security (mandatory) | Every SOC 2 examination |
| Availability | You guarantee uptime SLAs or 24/7 access |
| Processing Integrity | You process transactions or calculations for customers |
| Confidentiality | You handle proprietary customer data beyond PII |
| Privacy | You collect, use, or disclose personal information |
Document your system boundary
Your system boundary defines which infrastructure components, applications, and processes fall within your SOC 2 examination scope. You document every server, database, third-party service, and business process that supports the services covered by your report. The 2018 Description Criteria from the AICPA SOC 2 Guide requires you to describe your system's infrastructure, software, people, procedures, and data in your final report.
Start by listing your production environment components: application servers, databases, authentication systems, monitoring tools, and backup infrastructure. Include third-party services like your cloud hosting provider, email delivery service, and payment processor. Document which corporate systems you exclude from scope, such as internal HR systems or separate product lines that don't touch customer data.
Select Type 1 or Type 2 examination
Type 1 examinations evaluate whether your controls are designed appropriately on a specific date. Type 2 examinations test both design and operating effectiveness over a period (usually 6-12 months). You choose Type 1 for your first examination to validate your control design before committing to months of evidence collection, then pursue Type 2 for your renewal to demonstrate sustained compliance.
"Most health systems require Type 2 reports because they need proof your controls operated effectively throughout the examination period."
Step 2. Translate SOC 2 criteria into controls
You translate the abstract trust services criteria into specific control activities that your organization performs to meet each requirement. The 2017 Trust Services Criteria (revised 2022) contains 64 points of focus that describe what auditors evaluate, but you need to document the actual procedures your team executes. This translation process converts conceptual security requirements into testable controls your auditor can examine during fieldwork.
Map criteria to control activities
Each trust services criterion requires you to implement one or more control activities that address the underlying requirement. You start with the security category's common criteria (CC sections in the AICPA SOC 2 Guide), then add category-specific criteria based on your scope. Your controls must cover all relevant points of focus within each criterion you select.
Here are examples of how you translate criteria into implementable controls:
| Trust Services Criterion | Control Activity Example |
|---|---|
| CC6.1 (Logical Access) | Require multi-factor authentication for all production system access and review access logs weekly |
| CC6.6 (Encryption) | Encrypt all data in transit using TLS 1.2+ and encrypt databases at rest using AES-256 |
| CC7.2 (System Monitoring) | Deploy automated intrusion detection systems and configure alerts for suspicious activity |
| CC8.1 (Change Management) | Require pull request approvals from two engineers before merging code to production branches |
| A1.2 (Availability Monitoring) | Monitor system uptime every 60 seconds and maintain incident response procedures for outages |
Build your control documentation
Your control documentation describes the what, who, when, and how of each control activity. You create a control matrix that lists every control, its objective, the person responsible for execution, the frequency, and the evidence your auditor will review. This matrix becomes your operational playbook and your auditor's testing roadmap.

Document each control using this format:
Control ID: AC-001
Control Objective: Prevent unauthorized access to production systems
Control Activity: Security team reviews and approves all production access
requests within 24 hours using ServiceNow tickets
Control Owner: Director of Security
Frequency: Event-driven (each access request)
Evidence: ServiceNow approval tickets with timestamps and approver names
Your control descriptions must specify observable actions that produce verifiable evidence. Avoid vague statements like "we maintain secure systems" and instead write "engineers rotate database passwords every 90 days using our password manager."
"Controls must be specific enough that your auditor can determine whether the control operated by examining the evidence you provide."
Assign control owners and frequency
You assign a control owner to each control who becomes accountable for executing the control and maintaining evidence. Control owners are typically directors or managers who have authority over the process area, not individual contributors who perform daily tasks. The owner ensures the control operates at the defined frequency, whether that's daily, weekly, quarterly, or event-driven based on triggers like access requests or code deployments.
Map your controls to your existing team structure rather than creating new roles. Your engineering director owns development controls, your security lead owns access controls, and your operations manager owns monitoring controls. Each owner maintains a folder of evidence artifacts that demonstrate their controls operated throughout the examination period.
Step 3. Prepare for the SOC 2 examination
You prepare for your examination by organizing evidence, conducting a readiness assessment, and executing the formal audit fieldwork. Your auditor needs access to three to twelve months of control evidence depending on whether you pursue Type 1 or Type 2. The AICPA SOC 2 Guide specifies that auditors must test a representative sample of control instances across your examination period, so you need complete documentation before scheduling your kickoff meeting.
Organize your evidence repository
You create a structured folder system that maps directly to your control matrix. Each control gets its own folder containing all evidence artifacts the auditor will sample. Your evidence includes screenshots of system configurations, export files from monitoring tools, approval tickets, training completion records, and meeting minutes that demonstrate control execution.

Structure your evidence folders using this hierarchy:
SOC2_Evidence/
├── CC6_Logical_Access/
│ ├── AC-001_MFA_Configuration_Screenshots/
│ ├── AC-002_Access_Review_Reports/
│ └── AC-003_Termination_Tickets/
├── CC7_System_Operations/
│ ├── SO-001_Vulnerability_Scan_Reports/
│ ├── SO-002_Patch_Management_Logs/
│ └── SO-003_Backup_Verification_Records/
└── CC8_Change_Management/
├── CM-001_Code_Review_Pull_Requests/
└── CM-002_Change_Approval_Tickets/
Schedule your readiness assessment
You conduct an internal gap assessment 60 to 90 days before your formal examination begins. You review every control against the evidence you collected and identify any missing artifacts or control failures. Many organizations hire their audit firm to perform this readiness review using the same testing procedures they will apply during the actual examination.
"A readiness assessment lets you fix control gaps before your auditor finds them during fieldwork, which prevents report qualifications."
Execute the examination fieldwork
Your auditor schedules a kickoff meeting to review your system description, confirm the examination scope, and request their initial evidence samples. Fieldwork typically takes two to four weeks depending on your organization's size and the number of trust services categories in scope. You respond to evidence requests within 48 hours and schedule interviews with your control owners so the auditor can validate control procedures.
Ongoing SOC 2 governance and operations
You maintain your SOC 2 compliance by treating it as an ongoing operational program rather than a one-time audit project. Your controls must operate continuously between examinations, and you need to collect evidence every day so you're ready when your annual renewal begins. The AICPA SOC 2 Guide requires your auditor to test controls across the entire examination period, which means gaps in your evidence create report exceptions even if your controls work perfectly today.
Run monthly compliance reviews
You schedule monthly control reviews where each control owner confirms their controls operated as designed and uploads new evidence to your repository. Your security team runs these review meetings using a checklist that covers all controls in your matrix. Document any control failures immediately with root cause analysis and remediation plans, because your auditor will ask about exceptions during fieldwork.
Create a monthly review checklist that tracks:
- All access reviews completed on schedule
- Vulnerability scans executed and remediated
- Backup verifications performed successfully
- Code reviews approved before deployment
- Security training completed by new hires
- Vendor assessments conducted for new subservice organizations
Update your system description quarterly
You revise your system description every quarter when you make significant changes to your infrastructure, applications, or business processes. Your auditor compares your current system against the description in your last report, so outdated documentation creates control gaps. Update your system boundary diagram, vendor list, and data flow descriptions whenever you add new services or migrate infrastructure components.
"Maintaining accurate system documentation throughout the year prevents scrambling to document changes when your next examination starts."
Tie it all together
The AICPA SOC 2 Guide provides the examination framework your auditor follows, but you turn that framework into a passing report by implementing specific controls, collecting evidence daily, and maintaining governance between audits. You define your scope based on customer requirements, translate trust services criteria into testable control activities, prepare comprehensive evidence for fieldwork, and run continuous compliance reviews that keep your program examination-ready year-round.
Healthcare vendors need SOC 2 compliance to win health system contracts, but building compliant infrastructure takes time away from your core product. VectorCare provides a SOC 2-compliant platform for healthcare vendors building SMART on FHIR integrations with EPIC. You deploy your application on infrastructure that already meets SOC 2 requirements, which lets you leverage our compliance work instead of building your own program from scratch. Your customers get the security assurances they require while your team focuses on delivering clinical value rather than managing attestation examinations.
The Future of Patient Logistics
Exploring the future of all things related to patient logistics, technology and how AI is going to re-shape the way we deliver care.